Nmap: Network Scanning Tool
Nmap, short for Network Mapper, stands as a prominent open-source tool used for network scanning and security assessment.
Created by Gordon Lyon, who is often referred to by his alias Fyodor, Nmap has earned a reputation as a reliable resource in the fields of cybersecurity and network management.
The core functionality of Nmap involves sending packets to a designated target and interpreting the replies received.
This process facilitates the mapping of devices connected to a network, revealing which services they provide and highlighting any associated security vulnerabilities.
It is compatible with various operating systems, including Linux, Windows, and macOS.
One of the key applications of Nmap is in network discovery, which helps in identifying devices and their corresponding IP addresses within a local area network (LAN) or on broader networks like the internet.
This capability is vital for network administrators, allowing them to oversee network health and detect unauthorized devices that may have been introduced.
Additionally, Nmap is effective for port scanning, a method used to uncover open ports on a target device.
Since these ports can be exploited by cybercriminals, recognizing them is crucial for maintaining network security.
Nmap is equipped with a diverse range of scanning techniques, from basic ping sweeps to more sophisticated approaches such as SYN scans and OS fingerprinting.
These methods enable users to acquire comprehensive insights into a network, including the operating systems in play and the versions of software installed on various devices.
Moreover, Nmap incorporates a scripting engine (NSE) that allows for the automation of scanning activities and the identification of vulnerabilities.
This adaptability makes it an indispensable tool for security experts engaged in penetration testing as well as for network administrators overseeing extensive systems.
As a command-line utility, Nmap serves as a potent resource for analyzing networks, conducting security audits, and assessing vulnerabilities.
Its significance in the realm of cybersecurity and network management cannot be overstated.
Network analyzers like Nmap play a crucial role in enhancing network security for multiple reasons.
They are instrumental in identifying potential attackers and assessing vulnerabilities present in a network.
In the realm of cybersecurity, possessing extensive knowledge about packet traffic equips individuals and organizations to better prepare for possible attacks.
Regularly scanning your network is essential to stay vigilant against potential threats. Nmap is a powerful tool utilized for network analysis and packet sniffing, renowned for its flexibility.
With Nmap, users can effortlessly scan active IP addresses within their network.
If you encounter an unfamiliar IP, running a scan can help determine if it belongs to a legitimate service or is part of a potential external threat.
Network administrators often turn to Nmap due to its extensive features, all available at no cost.
Here are some key functionalities you can leverage with Nmap:
-
Discover live hosts on your network.
-
Detect open ports.
-
Determine the operating systems of services.
-
Identify vulnerabilities within your network setup.
Next, let’s discuss the installation process for Nmap.
Users of Windows, Linux, and macOS can download Nmap easily.
For Windows, utilize the self-installer file (named nmap-
Linux users have a bit more complexity, as they can choose between installing from source code or using various binary packages.
Installing Nmap on Linux enables the creation of custom commands and scripts.
To check if Nmap is already installed on Ubuntu, execute the command
nmap --version
.
If Nmap is not installed, simply enter
sudo apt-get install nmap
in the terminal.
For macOS, a specific installer is available.
To install Nmap, double-click on the nmap-
nmap-
file to initiate the installation.
If you are using OS X 10.8 or newer, your system may block the installation due to security settings regarding unidentified developers.
To bypass this, right-click the .mpkg file and select 'open'.
A fundamental aspect of managing a network is identifying active hosts.
In Nmap, this is accomplished with a ping scan, which helps determine if specific IP addresses are active.
Ping scans can also serve as a method for discovering hosts, with ARP ping scans being particularly effective for local area networks (LAN).
To carry out an ARP ping scan, input the following command in your terminal:
nmap -sp 192.100.1.1/24
This command will generate a list of hosts that responded to your ping requests, along with a total count of IP addresses at the conclusion of the scan.
It's essential to understand that this search does not transmit packets to the specified hosts. Instead, Nmap performs a reverse DNS lookup on these hosts to retrieve their corresponding names.
When it comes to scanning ports, Nmap offers several techniques. Here are the primary ones you can utilize:
-
ss- TCP SYN Scan -
st- TCP Connect Scan -
su- UDP Scan -
sy- SCTP INIT Scan -
sn- TCP Null Scan
Many beginners rely heavily on SYN scans to troubleshoot various issues. However, as you gain experience, you'll find it beneficial to explore these alternative techniques as well. It's worth mentioning that only one scanning method can be employed at a time, although combining SCTP and TCP scans is permissible.
TCP SYN Scan (ss)
The TCP SYN scan is known for its speed and efficiency, capable of scanning numerous ports each second on networks that lack firewall protection.
This method is also considered
privacy-conscious
since it does not complete TCP connections, thereby reducing the likelihood of drawing attention to your scanning activities. The process involves sending a SYN packet and awaiting a response:
- An
ACK
response signifies an open port,
- No response indicates a filtered port,
- An
RST
or reset suggests a non-listening port.
TCP Connect Scan (st)
The TCP Connect Scan serves as the primary alternative when a SYN scan is not feasible. In this method, the user initiates a connect system call to establish a connection with the network. Unlike the SYN scan, Nmap analyzes this call to gather data about each connection attempt instead of scrutinizing packet replies.
A significant drawback of the TCP Connect Scan is that it often takes more time to identify open ports compared to the quicker SYN scan.
UDP Scan (su)
For effective UDP service port scanning, you should utilize UDP scans.
These scans are essential for probing services like DNS, SNMP, and DHCP, which are often targeted by attackers.
When performing a UDP scan, you can also conduct a SYN scan concurrently.
A UDP scan involves sending packets to each designated port, usually empty packets, except for specific ports like 53 (DNS) and 161 (SNMP).
If no response is received after sending the packets, that port is deemed open.
SCTP INIT Scan
The SCTP INIT scan is designed for assessing SS7 and SIGTRAN services, utilizing both TCP and UDP protocols.
This scan is notably rapid, capable of scanning thousands of ports within a second.
It's an excellent option for those requiring discretion, as it does not complete the SCTP handshake process.
The method involves sending an INIT chunk and waiting for a reply.
If the target responds with an INIT-ACK chunk, the port is considered open; an ABORT chunk indicates a closed port.
If there is no response after several attempts, the port will be marked as filtered.
TCP NULL Scan
A TCP NULL scan is a subtle scanning technique that takes advantage of a vulnerability in TCP RFC regarding port states.
This method sends packets that lack SYN, RST, or ACK bits.
If a port is closed, it will respond with an RST packet; if open, there will be no response at all.
This stealthy approach allows you to bypass router filters and firewalls, although it may still be detectable by intrusion detection systems (IDS).
To discover active hosts within a network, a host scan is your best bet.
This scan sends ARP request packets across the network.
By targeting a specific IP range, any active host will reply with an ARP packet, providing its MAC address along with a message indicating that the host is operational.
To execute a host scan, use the following command:
nmap -sp
Executing this will display a screen with the results.
One of the most straightforward yet powerful commands in Nmap is the -sl option. This command enables you to perform a DNS query on any specified IP address. The beauty of this method is that it allows you to uncover hostnames associated with an IP without transmitting any data to that host. For instance, you can execute the following command:
nmap -sl 192.100.0.0/24
This will provide you with a list of names related to the IPs scanned, which can be extremely helpful for understanding the purposes of certain IP addresses, provided they have corresponding names.
Another key feature of Nmap is its ability to detect the operating system of a device. This is accomplished by sending TCP and UDP packets to a specific port and evaluating the responses received. Nmap conducts various tests, such as TCP ISN sampling and IP ID sampling, comparing the results against its extensive database of over 2,600 operating systems. If a match is found, Nmap will present a summary that includes the name of the provider, the operating system, and its version.
To identify the operating system of a particular host, you can use the following command:
nmap -o 192.168.5.102
Keep in mind that for the
-o
command to work, you must have both an open port and a closed port available.
Version detection is another valuable capability of Nmap. It allows you to ascertain the software versions running on a computer. Unlike many other scans, version detection does not concentrate on the port itself; instead, it focuses on identifying the software based on the information provided by an open port. You can activate version detection by using the
-sv
command followed by the desired IP address, like this:
nmap -sv 192.168.1.1
Additionally, when conducting scans with Nmap, you may want to gain more insights into the scanning process. The verbose flag, -v, offers extra information about what Nmap is doing during the scan. Nmap features nine different verbosity levels, ranging from -4 to 4:
- Level -4: No output, meaning response packets are not displayed.
- Level -3: Similar to -4 but includes error messages to indicate any failed Nmap commands.
- Level -2: Adds warnings and further error messages to the previous level.
- Level -1: Displays runtime details such as the version, start time, and statistics.
Nmap Verbosity and Scripting
-
Verbosity Level 0: This is the standard setting, showing basic information about the packets sent and received.
-
Verbosity Level 1: Similar to Level 0, but adds insights into protocol details, flags, and timing aspects.
-
Verbosity Level 2: Offers a deeper look into the packets exchanged, providing extensive details.
-
Verbosity Level 3: Displays the complete raw data transfer of the packets involved.
-
Verbosity Level 4: Expands on Level 3 by including even more comprehensive information.
Enhancing verbosity levels is beneficial for improving your scanning efficiency. By revealing more detailed information, it allows for targeted enhancements to your network setup.
To fully utilize Nmap's capabilities, the Nmap Scripting Engine (NSE) is essential. NSE enables users to create scripts using Lua, facilitating the automation of various networking processes. The scripts can be categorized into several types:
-
Auth: Scripts designed to interact with or bypass authentication on target systems (e.g., x11-access).
-
Broadcast: Used for discovering hosts through local network broadcasts.
-
Brute: Employs brute force tactics to access remote servers (e.g., http-brute).
-
Default: Predefined scripts in Nmap chosen for their speed, utility, verbosity, reliability, and respect for privacy.
-
Discovery: Scripts that probe public registries, directory services, and SNMP-enabled devices.
-
Dos: Scripts that can induce denial of service, useful for testing or attacking services.
-
Exploit: Targeted scripts that seek to leverage network vulnerabilities (e.g., http-shellshock).
-
External: Scripts that transmit information to outside databases like whois-ip.
-
Fuzzer: Sends randomized data within packets for testing.
-
Intrusive: High-risk scripts that may crash the target system and could be flagged as malicious by other administrators.
-
Malware: Used to ascertain if a system is infected with malware.
-
Safe: Non-intrusive scripts aimed at exploiting vulnerabilities without causing service crashes.
-
Version: Related to version detection but not selectable on its own.
-
Vuln: Scripts built to identify vulnerabilities and communicate findings to the user.
Initially, the NSE may appear complex, but with time and practice, it becomes easier to understand and use effectively.Utilizing Nmap effectively requires an understanding of its script capabilities. For instance, the command -sc enables access to common scripts that come with the tool. If you wish to implement your own scripts, the –script command is the way to go. However, caution is advised; running scripts can potentially harm your system, so it’s crucial to verify their safety before execution.
While Nmap is a favorite among seasoned users, it does come with certain drawbacks. Many beginners in network management anticipate a graphical user interface (GUI) from their tools, coupled with better visual representations of network performance metrics. The ported version known as en-map significantly addresses these expectations.
If command line tools are not your preference, there are several alternatives to Nmap worth exploring. For example, SolarWinds is a prominent provider of network management solutions and features a capable port scanner. Nmap’s analytical capabilities are somewhat limited, prompting users to seek additional tools for a deeper understanding of their network’s performance and status.
Despite being primarily a command line tool, Nmap faces competition from various systems that offer a more modern GUI. Many users find these alternatives preferable compared to Nmap's more traditional interface.
Here are some recommended alternatives to Nmap:
-
Site24x7 Network Monitoring : This cloud-based platform offers a 30-day free trial, allowing for device status checks and traffic analysis through network discovery routines.
-
Zenmap : Developed by the creators of Nmap, this is the official GUI version that provides solid mapping services across multiple operating systems, including Windows, Linux, macOS, and Unix.
-
Paessler PRTG : A comprehensive network monitoring solution that includes SNMP for device discovery and exceptional network mapping capabilities, designed for Windows Server.
-
Datadog Network Device Monitoring : Part of a SaaS platform, this module features device discovery and ongoing status checks utilizing SNMP.
-
Progress WhatsUp Gold : This performance monitoring tool employs SNMP for discovering all connected devices, creating an inventory and topology map, and it offers continuous monitoring, compatible with Windows Server.
In evaluating these network discovery tools, we focused on several key criteria:
-
An autodiscovery feature for compiling an asset inventory.
-
Effective topology mapping capabilities.
-
Live monitoring of network devices.
-
Utilization of SNMP for status information extraction.
-
Alerts for performance-related issues.
-
Availability of a free trial or demo for cost-free evaluation.
-
Overall value for money, ensuring that the service provides cost savings through enhanced productivity.
Site24x7 offers a comprehensive solution for network monitoring, encompassing both device oversight and traffic analysis.
This service efficiently identifies all devices within your network, creating an inventory and a detailed topology map.
It monitors the activity of each device individually as well as at the port level, ensuring granular insights.
Key Features Include:
- Monitoring the status of devices
- Analyzing traffic patterns
- Automatic discovery of devices
As a cloud-based platform, Site24x7 provides similar functionalities to the Datadog monitoring suite. However, unlike Datadog, which requires a separate purchase for network performance monitoring, Site24x7 incorporates traffic monitoring within its package.
Utilizing SNMP, Site24x7 tracks activities across switches, routers, and firewalls. In addition, it employs NetFlow and other technologies to analyze network traffic trends.
This all-in-one package not only covers device monitoring but also assesses the performance of various components, including VPNs, voice networks, load balancers, wireless access points, and office peripherals like printers and UPS systems.
Both the network inventory and topology map are interactive, allowing users to delve into device specifics and real-time activity.
The dashboard facilitates the establishment of performance thresholds, triggering alerts upon deviation. Alerts are also generated if an SNMP device agent detects a problem and sends a trap warning.
Beyond network monitoring, the Site24x7 platform encompasses server and application monitoring, offering a selection of service bundles. All plans inherently include network monitoring features.
Additional offerings within some bundles may include log management, synthetic monitoring, and real user monitoring for websites, tailored for varying business sizes—small businesses can opt for smaller packages, while larger enterprises can select those with greater capacity.
Key Benefits Include:
- Network monitoring integrated with server and application oversight
- Automatic topology mapping
- Monitoring capabilities for both wired LANs and wireless systems
- Plans with limited monitoring capacity, available for expansion through additional payments
Being a cloud platform, Site24x7 can monitor any network globally, provided a data gathering program is installed locally.
Users can explore this monitoring solution with a complimentary 30-day trial.
Start your 30-day free trial with Site24x7 network monitoring today!
Zenmap serves as the official graphical user interface (GUI) for Nmap, offering a user-friendly approach to network mapping without any cost. This tool is ideal for users seeking a budget-friendly option for network monitoring, making it particularly suitable for small businesses, although it can effectively manage larger networks as well.
Key functionalities include:
-
Bundled installation with Nmap
-
Command generator for Nmap
-
Automatic network discovery
-
Compilation of network assets
-
Real-time network mapping
For those who prefer a visual interface over command line operations, Zenmap provides an excellent alternative. Developed by the same team behind Nmap, Zenmap relies on Nmap for its underlying functionalities, allowing users to leverage the power of Nmap while enjoying visual representations of their network.
Zenmap offers a comprehensive view of devices within a network, utilizing color-coded indicators to represent the status of switches and routers. This feature allows for a swift health check of network components. However, it may not match the depth of monitoring capabilities found in premium solutions.
While tech-savvy users may appreciate the ability to engage with query languages, network managers pressed for time may find this tool's limitations somewhat frustrating. Despite being a reliable tool, it does feel somewhat outdated.
As a no-cost solution, Zenmap is particularly attractive to small businesses looking to implement network monitoring without financial investment. Although Nmap is favored by security professionals for scripted operations, Zenmap does not possess this feature, yet users can seamlessly transition between both tools for thorough network analysis.
Additional features encompass:
-
Compatibility with Nmap
-
Ad-hoc investigation capabilities
-
Script creation in Nmap's query language
-
Ideal for budget-conscious small businesses
-
Packet capturing functionality
-
Limited network monitoring capabilities due to its age
Zenmap is compatible with various operating systems, including Windows, Linux, macOS, and Unix, and is available for free download.
Network Monitoring Solutions Overview
Zenmap stands out as the leading alternative to Nmap, offering the same powerful features with a user-friendly graphical interface.
If the command-line interface of Nmap is what you find unappealing, Zenmap is the perfect solution for you.
This tool enables you to conduct network scans and visualize all connected devices along with their current statuses on an interactive map.
You can easily download Zenmap at no cost.
For more information, visit the official website: https://nmap.org/download
Supported operating systems include Windows, macOS, Linux, and Unix.
Paessler PRTG Network Monitor utilizes the Simple Network Management Protocol (SNMP) to identify and monitor devices across your network in real-time.
Once devices are detected, they are cataloged in an inventory, which serves as the foundation for your PRTG network visualization.
You have the flexibility to manually rearrange this map and create custom layouts.
Importantly, the maps are not confined to a single location; they can encompass devices across a Wide Area Network (WAN) and even represent your organization’s sites on a global map.
Additionally, cloud services can be integrated into the network visualization.
Key Highlights:
- Network Discovery
- Network Inventory and Topology Mapping
- Real-Time Network Monitoring
PRTG is a comprehensive monitoring tool for networks, servers, and software, centered around its network discovery functionality.
This feature generates a detailed inventory that rivals the information provided by Nmap.
Moreover, it includes a topology map that illustrates the network's structure.
The network discovery process operates continuously, ensuring that any changes—such as the addition, relocation, or removal of devices—are immediately reflected in both the network map and inventory.
Each device on the map is marked with its IP address; however, you can also choose to display them using MAC addresses or hostnames.
The icons representing devices are clickable, leading to detailed information about each piece of equipment.
You can customize the display of the network map to focus on specific device types or particular segments of the network.
PRTG serves as an integrated infrastructure monitoring system, tracking not only your servers but also the applications they host.
It includes specialized modules for website monitoring and extends coverage to virtualized environments and Wi-Fi networks.
Pricing for PRTG is based on the number of activated sensors, with a minimum purchase of 500 sensors.
If you activate only 100 sensors, you incur no charges for the system, making it an appealing option for businesses, particularly smaller ones.
Additional Features:
- Options for on-premises deployment or Software as a Service (SaaS)
- Continuous network monitoring with real-time updates to inventory and mapping
- Alerts for issues with network devices
- Not a free solutionPaessler PRTG can be accessed as an online service, which requires the installation of a local collector agent on your machine.
Alternatively, you have the option to deploy the software directly on your own hardware.
While PRTG is designed to operate on Windows systems, it has the capability to interact with devices that use different operating systems.
You can try out PRTG by downloading it through their free trial offer.
Datadog offers a comprehensive solution for monitoring network devices, distinct from its network performance monitoring service, which emphasizes traffic analysis.
Key features include:
- Automatic device discovery
- Detailed port mapping
- Continuous health assessments
As a cloud-based platform, Datadog’s network device monitoring requires a subscription, unlike the free tool Nmap. It generates a visual representation of the network, similar to the PRTG network map, by creating an inventory through an autodiscovery feature that catalogs each device and its interfaces.
The monitoring system actively scans the network to identify all connected switches and routers, collecting specifics such as manufacturer and model. It also identifies connected devices per port, ensuring a thorough overview of the network's infrastructure.
Throughout its operation, the network device monitor employs SNMP protocols to continually assess the health of network equipment. It solicits status updates from device agents and aggregates this data into real-time performance metrics displayed in the Datadog console, which includes graphical and tabular representations.
The system is designed to alert users when device agents encounter issues and establishes performance thresholds across all collected metrics, allowing for customizable notifications and dashboard arrangements.
While there is a cost associated with this system, it remains budget-friendly, particularly for smaller enterprises, with subscription fees based on the number of devices monitored. The tool automatically refreshes its inventory upon discovering new devices, enhancing security by identifying unauthorized devices.
Additional features include:
- Real-time device performance tracking
- Automated monitoring with customizable alerts
- Forecasting capabilities for future performance
- Separate module for traffic analysis
Datadog operates on a subscription basis, requiring the installation of an agent within the network to collect necessary data. Prospective users can evaluate the platform through a 14-day free trial.
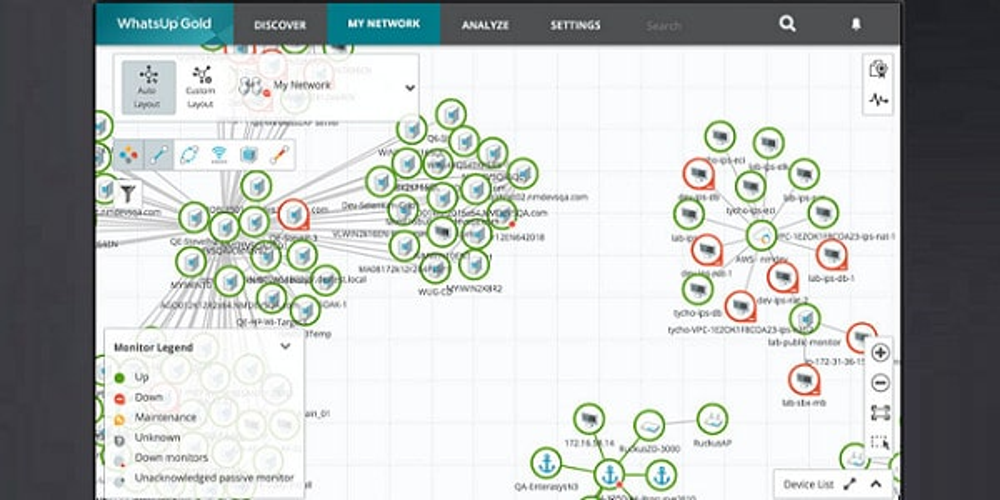
WhatsUp Gold serves as a robust real-time network monitoring solution equipped with an autodiscovery feature, designed to encompass wired, wireless, and virtual setups.
This infrastructure monitoring software is compatible with Windows Server editions including 2008 R2, 2012, 2012 R2, and 2016. Upon its initial launch, the tool initiates network discovery routines, which identify and document all Layer 2 and Layer 3 devices—like switches and routers—within your network.
During this discovery, a comprehensive network map is generated, continuously updated to reflect any modifications in the network landscape. Additionally, it incorporates any cloud-based services utilized by your organization and can aggregate multiple sites onto a single WAN map.
Notable features include:
- Based on SNMP (Simple Network Management Protocol)
- Automatic discovery of network devices
- Generation of a detailed network inventory
- Real-time network topology mapping
WhatsUp Gold is primarily an on-premises monitoring solution, emphasizing network discovery. It includes features for inventory tracking and equipment status updates, similar to the functionalities offered by Nmap. The system can be further enhanced with additional monitoring service add-ons.
The discovery mechanism of WhatsUp Gold relies on Ping and SNMP protocols, ensuring that various device types are logged. This allows the monitoring system to optimize its processes based on the specific equipment. Detailed popups associated with each device icon on the map provide insights into the equipment's status.
Device health is visually represented on the map, with a color-coding system: green indicates optimal performance, yellow signals warnings, and red denotes issues. This color-coded approach also applies to network link statuses, allowing users to quickly assess the overall health of their network.
Ideal for medium-sized businesses, WhatsUp Gold operates on Windows Server and simplifies setup through its autodiscovery functionality. While it may be suitable for smaller enterprises, it's important to note that this is a paid solution, which may lead budget-conscious businesses to consider free alternatives.
Key attributes include:
- On-premises software for Windows Server
- Continuous updates for network inventory and mapping
- Adaptable for networks of various sizes
- Provision of real-time network monitoring
- No SaaS (Software as a Service) version availableFor a comprehensive analysis of your network performance, consider enhancing your setup with a network traffic analysis add-on compatible with WhatsUp Gold. This tool empowers you with in-depth insights, enabling better troubleshooting through detailed evaluations of network performance at both the link level and end-to-end.
To manage resource allocation effectively, a capacity planning scanning tool is invaluable, as it forecasts demand and highlights areas for resource expansion.
If your goal is to pinpoint systems within your network while maneuvering around firewalls, Nmap is your go-to solution. While it may lack the flashiness of other network analysis tools, Nmap is a foundational element in the toolkit of most IT administrators. The functionalities of ping scans and port scans merely scratch the surface of what Nmap can accomplish.
For those eager to explore Nmap further, a robust community website is available, packed with guides and resources to maximize your usage. Comprehensive documentation is accessible directly on Nmap’s official site. Once you navigate the initial learning curve, you will enhance your visibility into your network and bolster your defenses against potential threats. Start with the fundamentals, and you’ll find success in using Nmap.
It’s crucial to note that scanning ports on your own systems is entirely legal. Scanning the public-facing infrastructure of others is also permissible, provided you refrain from unauthorized access based on the data you gather from Nmap.
To engage aggressive scanning mode, simply use the -a command option. This activates a suite of features: OS detection (-o), version detection (-vs), script scanning (-sc), and traceroute (-traceroute). For convenience, using -a will enable all four functions simultaneously.
On average, Nmap requires approximately 21 minutes to scan each host connected to your network.
For more resources, don’t hesitate to check out the Comparitech Nmap cheat sheet.
What is a Netflix VPN and How to Get One
A Netflix VPN is a virtual private network that enables users to access region-restricted content on Netflix by connecting to servers in various countries. By using a Netflix VPN, viewers can bypass geographic limitations and enjoy a wider selection of shows and movies available in different regions. To use a Netflix VPN, one must select a dependable VPN provider that supports streaming, set up an account, install the VPN application, connect to a server in the desired location, and then access Netflix for an expanded viewing experience.
Why Choose SafeShell as Your Netflix VPN?
If people want to access region-restricted content by Netflix VPN, they may want to consider the SafeShell VPN . One of the main reasons Netflix VPNs might not be working is due to outdated software that can't keep up with Netflix's detection mechanisms. SafeShell VPN, however, provides a reliable solution with its high-speed servers specifically optimized for Netflix. These servers ensure that users can enjoy uninterrupted, high-definition streaming of their favorite shows and movies. Additionally, SafeShell VPN's ability to connect multiple devices at once makes it versatile and convenient for households with various operating systems, including Windows, macOS, iOS, Android, Apple TV, Android TV, and Apple Vision Pro.
Moreover, SafeShell VPN offers an exclusive App Mode that allows users to access content from multiple regions simultaneously, broadening the horizons of available entertainment. With its lightning-fast speeds, users can say goodbye to buffering and throttling, enjoying seamless streaming and browsing experiences. Furthermore, SafeShell VPN prioritizes user security with its proprietary "ShellGuard" VPN protocol, providing advanced encryption and robust security features to protect online privacy. As a comprehensive and reliable option, SafeShell VPN stands out for anyone facing the issue of a netflix vpn not working effectively.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To enjo