Understanding Logical Ports
Logical ports serve as crucial components in network communications, functioning as virtual connection points for data exchange between devices and applications. These ports are numerically identified, spanning from 0 to 65535, and fall into two primary categories: TCP (Transmission Control Protocol) and UDP (User Datagram Protocol).
TCP ports provide reliable, connection-oriented communication channels that ensure accurate and sequential data delivery. This makes them particularly suitable for applications requiring data integrity, such as web browsing (port 80) and email services (port 25).
In contrast, UDP ports offer connectionless communication with enhanced speed, making them ideal for real-time applications like video streaming and DNS queries (port 53).
When applications or services await incoming connections, they utilize specific logical ports, commonly referred to as "open ports." For instance, web servers typically monitor TCP port 80 (HTTP) or 443 (HTTPS). While these open ports enable essential functionalities, they can create security vulnerabilities if inadequately protected.
Cybersecurity professionals employ port scanners to identify open ports and potential vulnerabilities. Several free port scanning tools are available for network administrators and security specialists:
PRTG by Paessler offers comprehensive port monitoring capabilities within its infrastructure monitoring system, with 100 free sensors and a 30-day trial period.
ManageEngine OpUtils combines IP address management with switch port monitoring, featuring a free version compatible with Windows Server, Linux, and AWS.
Zenmap provides free network security monitoring across multiple platforms including Windows, Linux, BSD Unix, and macOS.
For quick online scanning options, tools like PortChecker, Open Port Scanner, and IP Fingerprints Network Port Checker offer web-based alternatives without installation requirements.
Windows users can benefit from Free Port Scanner, Port Checker 1.0, and TCPView, which effectively monitor TCP ports and process activities.
Spiceworks IP Scanner presents a cloud-based solution with local agents for Windows, macOS, and Linux distributions.
Firewalls serve as critical security components by monitoring and controlling network traffic according to predefined rules, permitting only authorized communications through specific ports. Regular auditing of open ports is essential for maintaining robust security, as unnecessary open ports expand the potential attack surface for cybercriminals.
By understanding each port's function and systematically closing unnecessary ones, organizations and individuals can significantly reduce their exposure to network-based threats and strengthen their overall security posture.
We delved into the realm of port scanners, evaluating them based on several key features:
-
The capability to scan ports on a single device or multiple devices simultaneously
-
The option to check a specific port or a range of ports for open or closed status
-
The ability to conduct scans across an entire network, not just the local host
-
A feature that provides information about the protocol associated with each scanned port
-
The functionality to generate and export a list detailing the status of all scanned ports
-
Availability as a free tool, requiring no payment for usage
-
An efficient port mapping system that justifies the installation and setup process
In our search, we focused primarily on those port scanners that are available at no cost. We also paid special attention to tools that come with additional utilities beyond just scanning ports.
Comprehensive Network Monitoring with PRTG: Port Scanning and Beyond
PRTG by Paessler offers robust infrastructure monitoring capabilities that extend well beyond simple port scanning. This versatile system employs specialized sensors to monitor various aspects of your network environment, from devices and servers to applications.
Port Monitoring Capabilities
PRTG provides two distinct port monitoring options:
-
Individual Port Sensor: Monitors specific TCP ports on designated devices, reporting accessibility and response times
-
Port Range Sensor: Examines multiple ports simultaneously, either as continuous ranges or custom port lists
Both sensors deliver valuable insights into port status (open/closed) and connection performance metrics. The individual port sensor offers the additional benefit of TLS support for secure connection testing.
Network Discovery and Monitoring
Beyond port scanning, PRTG utilizes ping and SNMP protocols to:
-
Automatically discover network devices
-
Map network topology
-
Monitor switch ports
-
Track network traffic via NetFlow sensors
Comprehensive Infrastructure Monitoring
PRTG extends monitoring capabilities across:
-
Network devices and connections
-
Server performance
-
Application functionality
-
Dozens of additional metrics
Flexible Deployment Options
Users can implement PRTG as:
-
Windows server installation
-
Cloud-based service
Cost-Effective Solution
PRTG's pricing structure is based on sensor count:
-
Free tier: Up to 100 sensors
-
Paid plans: Starting at 500 sensors
-
30-day unlimited sensor trial available
The free tier makes PRTG particularly attractive for small businesses or organizations with limited monitoring needs. However, port monitoring can quickly consume sensor allocations since each IP/port combination requires a dedicated sensor.
Ideal Use Cases
PRTG is particularly well-suited for:
-
Organizations needing comprehensive infrastructure monitoring
-
Environments requiring long-term performance tracking
-
Networks benefiting from auto-discovery capabilities
-
Businesses seeking scalable monitoring solutions
While the platform offers exceptional functionality, new users should note the learning curve associated with its feature-rich interface and extensive capabilities.
ManageEngine OpUtils combines IP address management with switch port mapping functionality. While the term "switch port" might be confusing as it refers to physical cable connections rather than logical network ports, this comprehensive package includes a dedicated port scanner among its network tools.
The port scanner component allows users to examine logical computer ports, providing detailed information about each port's protocol and status. This feature complements the physical port mapping capabilities, creating a well-rounded network management solution.
With OpUtils, you can scan port ranges on specific devices identified by IP address, displaying which ports are open through on-demand scanning. The software doesn't continuously monitor ports but provides thorough information when scans are executed.
Beyond port scanning, OpUtils offers a network scanner and diagnostic tools. Its IP address management functionality generates reports on address usage, helping identify abandoned addresses, duplicates, and unauthorized devices on your network.
While OpUtils is primarily a commercial product, ManageEngine offers a 30-day free trial that includes the port scanner feature. The free edition only provides IP address scanning without port scanning capabilities. The software supports Windows Server and Linux installations, with an AWS service option available for the paid version.
The system excels at providing comprehensive port information, revealing not just open ports but also details about the services running behind them, making it valuable for network administrators who need in-depth visibility into their network infrastructure.
Nmap delivers comprehensive network analysis capabilities alongside Zenmap, its graphical counterpart, empowering users to explore device connectivity and service availability across networks.
'
As a cross-platform solution, it operates seamlessly on Windows, macOS, Linux, and BSD systems, offering flexibility for diverse IT environments.
'
The toolset extends beyond basic port scanning, enabling protocol-specific examinations (TCP/UDP), operating system fingerprinting, and service version detection for identified ports.
'
Stealth scanning techniques like SYN stealth allow discreet reconnaissance by avoiding full TCP handshakes, though comprehensive scans may require hours to complete for thorough results.
'
Zenmap simplifies complex Nmap commands through visual workflows while retaining access to advanced parameters, though newcomers might initially find both interfaces challenging to master.
'
Network administrators leverage its dual functionality for both infrastructure mapping and security audits, identifying unauthorized services or vulnerable port exposures.
'
Custom scan profiles range from quick ping-based checks to intensive multi-stage inspections, with intelligent logic that focuses deeper analysis on active ports detected during initial sweeps.
'
As open-source software backed by an active developer community, Nmap receives continuous updates addressing emerging network protocols and security research developments.
'
While primarily used for ethical network assessment, its powerful capabilities necessitate responsible usage adhering to local regulations and network ownership permissions.
Web-Based Port Scanner Overview
This web-based utility provides instant visibility into device connectivity by probing select ports accessible from external networks
Unlike traditional network scanners requiring local installation
PortCheckers operates entirely through browsers
making it ideal for quick remote diagnostics without software setup
The system evaluates 36 standardized ports across core internet protocols
including FTP (20/21), HTTPS (443), SSH (22), and DNS (53)
A condensed scan option targets 13 critical entry points
revealing potential vulnerabilities in real-time
Security analysts appreciate its ability to audit third-party systems
since scans aren't restricted to the requester's own devices
This external perspective helps identify exposed services
from email protocols (SMTP/POP3/IMAP) to legacy channels like Telnet
Results display in color-coded tables showing:
-
Active services with detected responses
-
Firewall-blocked connections
-
Filtered ports indicating potential security measures
While convenient for basic reconnaissance
the tool has notable limitations:
-
Partial port coverage (doesn't scan ephemeral ranges)
-
Less detailed service fingerprinting than Nmap
-
Single-port verification rather than batch analysis
Ideal use cases include:
• Verifying server configurations post-deployment
• Testing firewall rules for essential services
• Educational demonstrations of port behavior
As a free resource
it serves as entry-level alternative to advanced suites
though security professionals typically require more comprehensive solutions for thorough audits
The Web Tool Hub's Online Port Scanner: A Quick Review
This web-based port scanning utility offers a convenient way to check for open ports without installing any software. By simply entering your IP address and selecting up to 10 ports per scan, you can quickly identify which services are accessible from the internet.
The scanner presents results in a clear tabular format that displays each port's status alongside its standard service designation. While the 10-port limitation makes comprehensive scanning impractical (considering there are 65,535 possible ports), the tool does support range notation like "21-29" to streamline the process.
Notable advantages include:
• Browser-based access with no installation required
• Support for both TCP and UDP protocols
• Ability to export results to CSV format
• Quick response times for scan results
The port scanner is just one component of Web Tool Hub's broader suite of networking utilities, which includes:
• IP geolocation services
• Backlink analysis tools
• WHOIS lookup functionality
• Network ping testing
Limitations to consider:
• The 10-port maximum per scan makes extensive testing cumbersome
• Basic reporting capabilities only
• No ability to customize result sorting
• External scanning only—cannot detect ports on internal network devices
This tool is ideal for quick verification of specific ports but less suitable for security audits or comprehensive network analysis that would require examining hundreds or thousands of ports.
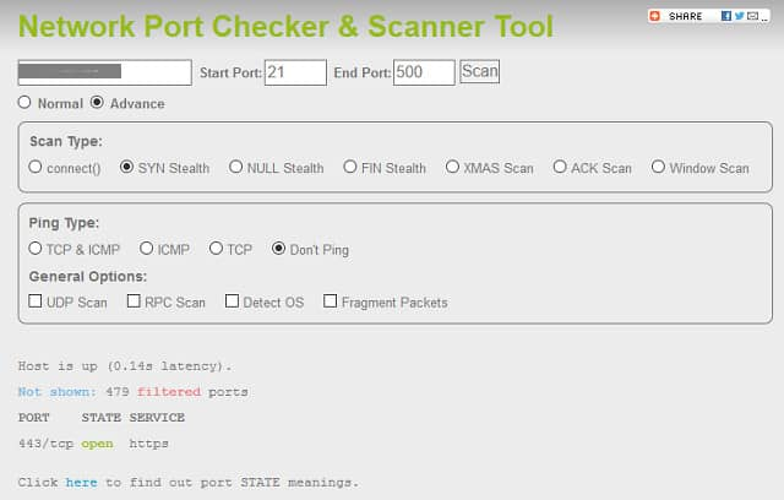
IP Fingerprints offers a comprehensive Network Port Checker and Scanner that serves as a valuable online security assessment tool. By simply entering an IP address and specifying a port range, users can quickly identify open ports on internet-connected devices.
While the platform recommends limiting scans to under 500 ports for optimal performance, our testing demonstrated relatively quick results even when pushing these boundaries. A scan of ports 21-500 completed in under a minute, though it's worth noting that detection capabilities may differ from local scanning tools like Nmap due to the external scanning perspective.
The scanner provides two distinct scanning modes. The Normal scan identifies ports visible from the internet versus those protected by firewalls. For more sophisticated analysis, the Advanced options include Connect() command tests and SYN Stealth scans—techniques frequently employed by security professionals and potential attackers during reconnaissance. The SYN method is particularly noteworthy as it mimics techniques commonly used in DDoS attack preparation.
Beyond port scanning, IP Fingerprints enhances its utility with additional network tools including geolocation services and WHOIS lookups, creating a well-rounded online security toolkit.
Key advantages include:
• Browser-based operation with no installation required
• Custom port range scanning capabilities
• Support for advanced scanning methodologies (SYN, ACK, FIN)
• Fragment packet scanning to evade detection systems
Limitations to consider:
• Extended scans exceeding 500 ports can become time-intensive
• Limited graphical reporting functionality
• External scanning perspective may miss internally visible ports
• Primary focus on internet-facing devices rather than internal network assets
This tool proves most valuable for external security assessments and understanding your network's exposure from an outside perspective.
This Windows-compatible network analysis tool requires installation from third-party platforms
Developed by NSASoft (though absent from their official site), the software provides basic port inspection capabilities
Automatic IP detection and preconfigured port lists simplify initial scans across local networks
Core functionalities include:
-
Sequential or custom port range examination
-
TCP protocol exclusivity (no UDP support)
-
Service identification for detected open ports
-
Local and internet-facing device scanning (excluding internal private networks)
Performance limitations emerge during extensive scans
Full port analysis on routers could span hours, requiring continuous operation
WiFi users must manually input network IPs for accurate device mapping
Interface considerations:
-
Straightforward navigation for beginners
-
Built-in service explanations enhance usability
-
Dated design affects multi-port scan efficiency
-
Banner advertisements present minor distractions
While outperforming agentless web scanners for internal networks
Its execution speed lags behind competitors
Closed port visibility lacks diagnostic context
No documentation clarifies scanning methodologies
System compatibility restricted to Windows OS
Freeware model sustains through third-party distribution channels
Suitable for basic network audits despite functional constraints
Available for Windows systems via Softpedia’s verified repository, Port Checker 1.0 offers a no-frills approach to port scanning while prioritizing security.
This standalone application skips complex installations—simply unzip the downloaded file and launch the executable directly or from a USB drive, making it ideal for on-the-go diagnostics.
Users input an IP address and choose from a predefined list of ports via dropdown, though custom entries or port ranges aren’t supported—a notable limitation for advanced users.
While designed for local network assessments, the tool can test internet-facing devices by targeting public IPs, helping troubleshoot router configurations or device accessibility.
Its minimalist design lacks modern features like auto-IP detection or filtering, but the lightweight footprint (under 1MB) ensures rapid deployment in time-sensitive scenarios.
Softpedia’s malware-free guarantee adds a layer of trust, though the single-port scanning method demands patience compared to bulk-scan alternatives.
Technicians may appreciate its portability and simplicity, but power users will likely seek more robust solutions for comprehensive network audits.
Network Scanning Tools Overview
What is My IP? offers a popular web service for IP address discovery alongside various tools including a port scanner available in both free and paid versions.
The port scanner allows external scans with reports on individual ports or selected groups from a pick list. While the free version has limitations, paid members can scan port ranges or create custom port lists.
One standout feature is the thematic "package" scanning option. This unique functionality lets users scan ports based on specific categories like gaming platforms, basic services (email, FTP), web services (HTTP, HTTPS), or ports commonly exploited by malware and hackers.
The scanner delivers impressively fast results for a web-based tool, with multiple port scans completing within seconds. However, it cannot penetrate your internal network and requires internet access to function.
The service complements What is My IP?'s core functionality, which helps users verify if they're using a proxy or VPN by displaying their public IP address and associated geographical information.
Key advantages include its speed, thematic scanning capabilities, and flexible port selection options. The main limitation is its dependency on internet connectivity at your testing location.
TCPView: A Process-Centric Network Monitoring Tool
TCPView offers a unique approach to monitoring network activity on Windows systems. Unlike conventional port scanners that probe ports to check for active services, TCPView examines running processes and identifies their associated network connections.
This Microsoft-developed utility provides comprehensive visibility into both TCP and UDP communications, displaying not only the processes listening on ports but also active connections with remote systems. The tool refreshes automatically, with customizable intervals of 1, 2, or 5 seconds.
Visual indicators enhance the monitoring experience—new processes appear highlighted in green, terminated processes in red, and status changes in yellow. For each connection, TCPView displays detailed metrics including packet counts and data transfer volumes.
The process-oriented interface reveals connections that might be missed by traditional port scanners, particularly those using non-standard port numbers beyond the well-known ranges. This makes TCPView particularly valuable for troubleshooting and security analysis.
While TCPView excels at monitoring the local system's network activity, it cannot scan remote computers directly. You'll only see information about remote ports when they're actively communicating with your machine.
Benefits include minimal resource utilization, intuitive color-coding, and comprehensive protocol support. However, users should be aware of the somewhat technical learning curve and limited reporting capabilities.
For system administrators and security professionals seeking to understand exactly what processes are communicating over the network, TCPView provides insights that external scanning tools simply cannot match.
Spiceworks IP Scanner: A Comprehensive Network Discovery Tool
The Spiceworks IP Scanner combines cloud-based dashboard functionality with a locally installed monitoring agent. This dual architecture provides comprehensive network visibility while maintaining data security through encrypted communications.
Installation and Platform Support
The monitoring agent is compatible with multiple operating systems:
• Windows
• Mac OS
• Ubuntu Linux
• Debian Linux
However, users should note that the dashboard interface cannot be accessed through Safari browsers.
Functionality Overview
Once configured, the scanner automatically discovers all devices on your network and reports essential information including:
• MAC addresses
• IP addresses
• Hostnames
• Manufacturer details
• Operating system identification
• Open port listings
The free version is supported by advertisements but requires no financial investment, making it particularly suitable for small businesses without dedicated IT resources.
Alternative Option: Spiceworks Port Scanner and Tester
For users seeking a simpler solution without software installation, Spiceworks offers a browser-based port scanner. This online tool checks port status for any specified IP address and works across all operating systems.
Advantages and Limitations
Pros:
• Cross-platform compatibility
• Comprehensive device discovery
• Excellent interface for monitoring ports and services
• Free to use
Cons:
• Requires local installation plus browser access
• Contains advertisements
• No Safari support
• Requires internet connectivity
Port Scanning: Online vs. Local Tools
External online scanners provide an outside perspective of your network, showing what potential attackers might see. Conversely, locally installed scanners reveal internal processes listening on ports.
The difference in detected services between these approaches demonstrates firewall effectiveness. For optimal security monitoring, using both types is recommended.
Understanding Network Ports
Ports function as network addresses with standardized assignments managed by the Internet Assigned Numbers Authority (IANA). They are categorized into three ranges:
-
Well-known ports (0-1023): Reserved for common services like HTTP and DNS
-
Registered ports (1024-49151): Allocated to proprietary applications
-
Private/ephemeral ports (49152-65535): Available for dynamic allocation
Network communications typically use either TCP (connection-based) or UDP (connectionless) protocols, with TCP being more common for port scanning due to its acknowledgment mechanisms.
Port states reveal critical network insights - open ports maintain active listeners (daemons),
while closed ports lack such processes. Firewalls create complexity by potentially blocking
both states through filtering rules unrelated to service availability.
TCP scanning fundamentals rely on three-way handshake manipulation. Traditional connect() scans
complete full SYN-SYN/ACK-ACK exchanges, whereas stealthy SYN scans abandon dialogues after
receiving initial acknowledgments. This half-open approach avoids full connection logs.
UDP port assessment proves trickier due to connectionless protocols. Null scans exploit ICMP
"port unreachable" errors for closed ports, though modern systems throttle these responses
to hinder reconnaissance efforts. Malformed packet techniques like Xmas scans (all flags set)
and FIN probes target OS-level inconsistencies, as proper services ignore irregular requests.
Advanced evasion tactics include packet fragmentation to bypass transport-layer inspections,
and glacial scanning speeds to avoid triggering intrusion thresholds. Ephemeral port monitoring
becomes crucial, as malware often establishes secondary channels through dynamic ranges after
initial well-known port contact.
Defensive systems counteract scans through SYN flood protection, connection rate limiting,
and stateful packet analysis. However, protocol loopholes persist - fragmented scans succeed
when firewalls neglect packet reassembly, while ACK scans exploit TCP's error handling for
firewall mapping without direct port access attempts.
Modern networks face dual challenges: distinguishing legitimate traffic from slow, distributed
scans while maintaining service availability. The arms race continues as scanning tools
adapt to new filtering techniques, and defenders enhance anomaly detection through machine
learning pattern recognition in packet streams.
Network diagnostics tools often bundle supplementary capabilities beyond basic port interrogation.
Consider ping utilities and DNS lookup functions – these extras transform simple scanners into comprehensive traffic analyzers.
Modern network gateways employ clever address translation tricks to maximize limited IP resources.
Port Address Translation (PAT) acts like a postal sorting system, appending unique identifiers to outgoing data packets.
This digital tagging allows multiple devices to share a single public IP while maintaining individual communication channels.
Temporary port allocation systems enable secure external access for specific applications.
Take instant messaging platforms: these services dynamically assign verification ports during sessions,
automatically closing these digital doors once transactions complete to prevent lingering vulnerabilities.
Cybersecurity professionals adopt adversarial mindsets to fortify defenses effectively.
Ethical hacking practices involve probing your own systems with port inspection utilities,
revealing potential entry vectors that malicious actors might exploit through unprotected communication channels.
Digital ports function as specialized mailrooms within network-connected devices.
Background processes monitor these numbered entry points,
activating only when packets arrive bearing their designated numerical tags.
Active monitoring utilities perform sequential knock checks on these virtual doors,
documenting which entrances respond to connection attempts.
Cybercriminals frequently target protocol-specific access points:
• File transfer portals (TCP 21)
• Secure shell entryways (TCP 22)
• Email protocol gateways (TCP 25/110)
• Web security tunnels (TCP 443)
Windows users can audit active connections through elevated command prompts:
-
Launch Terminal with administrative privileges
-
Execute netstat -ab to reveal listening services
-
Identify unprotected processes bound to external-facing ports
Complementary network security strategies should include:
Traffic pattern analysis through packet inspection tools
Real-time bandwidth consumption monitoring
Vulnerability assessment scanners for proactive threat detection
Understanding address translation mechanics and protocol-specific risks creates robust network defenses.
Regular port audits using multiple diagnostic methods – both local utilities and cloud-based scanners –
provide layered visibility into potential security gaps across private and public network interfaces.
What is a Netflix VPN and How to Get One
A Netflix VPN is a tool designed to help viewers overcome geographic restrictions by rerouting their internet traffic through servers in other countries. It enables access to exclusive regional libraries on Netflix, allowing users to stream shows and movies unavailable in their own location. By masking the user’s IP address, a Netflix VPN ensures broader content availability while maintaining privacy during streaming.
Why Choose SafeShell as Your Netflix VPN?
If you’re seeking a reliable VPN to access region-restricted Netflix content, SafeShell VPN is a standout choice.
-
SafeShell VPN ensures
Netflix unblocked
with high-speed servers tailored for seamless streaming, eliminating buffering and supporting HD playback across global libraries.
-
Its exclusive App Mode allows simultaneous access to multiple regional Netflix catalogs, expanding your entertainment options without switching configurations.
-
The VPN supports up to five devices at once, compatible with platforms like iOS, Android, smart TVs, and more, so your entire household can stream without compromise.
-
Built-in ShellGuard protocol offers military-grade encryption, safeguarding your data while you enjoy Netflix unblocked, free from ISP throttling or privacy risks.
-
A flexible free trial lets you test its lightning-fast speeds and user-friendly interface risk-free, proving its value before any commitment.
With these features, SafeShell VPN transforms how you experience