Browser extensions can greatly improve your internet usage, but they also carry potential security threats. Some of these extensions are designed with malicious intent, aiming to collect your private information, monitor your online activities, or even gain control over your device. This article will guide you through recognizing and eliminating harmful extensions to protect your online safety.
Often, malicious extensions disguise themselves as useful applications while executing harmful actions behind the scenes. They can harvest your data without your consent, clutter your browsing experience with unwanted advertisements, redirect you to dangerous sites, or degrade the performance of your browser. These risks can jeopardize your privacy, leading to serious consequences like identity theft or financial fraud.
The real threat lies in their ability to blend in seamlessly with legitimate extensions. Initially, they may seem innocent, but their true intentions usually reveal themselves after installation, especially once they gain access to your sensitive information. It’s essential to be cautious about which extensions you add and to frequently check the ones already installed in your browser.
To identify potentially harmful extensions, keep an eye out for these red flags:
Unknown Extensions : Regularly check your installed extensions and be wary of any that you don’t recognize.
Ambiguous Names : Be cautious of extensions with names that don’t clearly define their purpose.
Unjustified Permissions : Analyze why an extension requires specific permissions. For instance, a simple calculator shouldn't need access to your browsing data.
Sudden Browsing Changes : An uptick in pop-up ads, unexpected redirects, or a noticeable slowdown in browser performance can signal a malicious extension.
Negative Reviews or Low Ratings : Before adding an extension, look at user feedback and ratings. While these aren't foolproof, they can highlight potential problems.
Unauthorized Modifications : Extensions that alter your homepage, search engine, or other settings without your consent are likely harmful.
Unexpected Installations : If new extensions appear in your browser without your action, it may indicate a security breach.
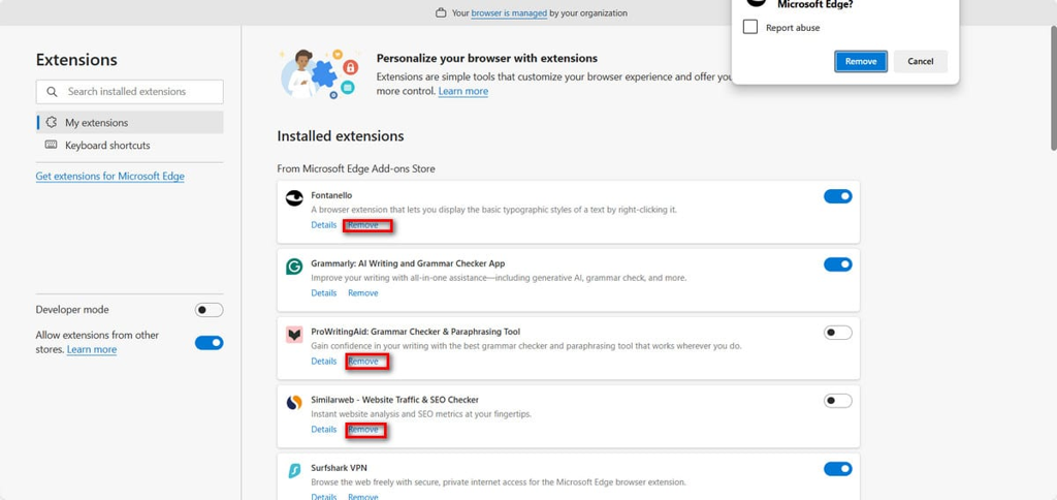
Removing suspicious extensions can differ slightly based on the browser you’re using. Here’s how to do it for some of the most widely used browsers:
After you have uninstalled any harmful browser extensions, make sure to restart your browser. This will help to solidify the changes made and eliminate any leftover processes.
It's wise to take additional precautions to safeguard your personal information, accounts, and identity. Malicious extensions often gather sensitive data and transmit it to cybercriminals.
For instance, the SearchBlox extension, which claimed to help users find Roblox players, was actually a front for hijacking accounts and stealing virtual assets, racking up over 200,000 downloads before its removal from the Chrome Web Store.
Similarly, Netflix Party and Netflix Party 2, meant to enable synchronized viewing experiences, were found to be tracking user activity and adding affiliate links to webpages.
Another notorious extension, Full Page Screenshot Capture, intended for capturing entire web pages, was revealed to monitor user data and modify cookie settings on shopping sites, also with more than 200,000 downloads prior to its exposure.
Other popular malicious extensions included Autoskip for YouTube, Crystal Ad Block, and Brisk VPN, which collectively had millions of users—9 million, 6 million, and 5 million, respectively.
Even the PDF Toolbox extension, boasting over 2 million users and favorable ratings, was discovered to load unverified code from questionable sites onto every web page accessed.
To reduce the chances of encountering harmful extensions in the future, consider the following steps:
Be cautious when installing new extensions. Always use official web stores and carefully assess each option. Check user reviews and ratings, but be aware that these can be manipulated.
Watch out for extensions that ask for excessive permissions. Think about whether the requested access is appropriate for the extension's purpose. If you're unsure, it's better to be safe than sorry.
Keep your browser and extensions updated. Regular updates are essential as they often include important security fixes.
Enable automatic updates to consistently run the latest, most secure versions available.
You might also want to use reliable antivirus software equipped with web protection capabilities. Such tools can add an extra layer of security against various online threats, including harmful extensions.
While most modern antivirus solutions can identify malicious browser extensions, they aren't infallible. New or advanced malicious extensions may evade detection. Thus, it's crucial to combine antivirus protection with careful browsing habits and proactive vigilance.Not every free browser extension is harmful, but they often carry a greater risk. Developers of these free tools may resort to monetization strategies like collecting user data or injecting ads. It’s essential to conduct thorough research on any extension prior to installation, regardless of its cost.
While many harmful extensions primarily affect your browsing experience, some advanced ones can gain access to your computer's file system and other applications. This highlights the importance of being discerning about the extensions you choose to install and the permissions you allow.
If you have doubts about a particular extension, consider disabling it temporarily to observe if any unusual behavior ceases. Investigate the extension online by searching for reviews and safety discussions. Additionally, utilize online virus scanning tools to inspect its files. If uncertainty persists, it’s prudent to uninstall the extension and look for a reputable alternative.
It’s important to note that not all extensions available in the Chrome Web Store are completely safe. Although Google implements security measures and a vetting process, some malicious extensions may evade detection. This can occur due to:
- The sheer volume of submissions, making thorough evaluation challenging.
- Cybercriminals continuously crafting new methods to bypass security protocols.
- Some extensions beginning as benign but turning harmful after updates.
- Malicious actions that only become noticeable after an extension has been widely used.
- Certain harmful extensions cleverly disguised as legitimate products.
To enhance your safety, consider these practices:
- Install only the extensions that you truly need.
- Conduct research on extensions before adding them (look for reviews and the reputation of the developer).
- Be wary of extensions that ask for excessive permissions.
- Keep your extensions updated regularly.
- Perform routine checks to remove any extensions that are no longer in use.
Keep in mind that while the Chrome Web Store is generally safer compared to third-party sources, it is not completely free from risks. Staying vigilant is essential for maintaining your browser's security.
What is a Netflix VPN and How to Get One
A Netflix VPN is a virtual private network that enables users to bypass geographical restrictions and access region-restricted content on Netflix by connecting to servers in various countries. By selecting a reliable VPN provider that supports streaming, users can create an account, download and install the VPN application, and connect to a server in the desired region to enjoy Netflix content that might otherwise be unavailable in their location.
Why Choose SafeShell as Your Netflix VPN?
If you want to access region-restricted content by using a Netflix VPN, you may want to consider the SafeShell VPN . One of the primary benefits of SafeShell VPN is its high-speed servers optimized specifically for Netflix streaming. These servers ensure you can enjoy your favorite shows and movies without interruptions, offering buffer-free playback and high-definition streaming. Additionally, SafeShell VPN allows you to connect up to five devices simultaneously, supporting a wide array of operating systems such as Windows, macOS, iOS, Android, Apple TV, and more. This ensures that you can enjoy your favorite content on any device you choose, enhancing your streaming experience.
Furthermore, SafeShell VPN's exclusive App Mode feature enables you to unlock and enjoy content from multiple regions at the same time, offering access to a diverse range of streaming services and libraries. With lightning-fast speeds and no bandwidth limitations, you can say goodbye to buffering and throttling, allowing for unprecedented internet performance. Moreover, SafeShell VPN prioritizes your online privacy with its proprietary "ShellGuard" VPN protocol, ensuring top-level security for your private browsing sessions. This advanced encryption and robust security feature give you the confidence to surf the web, knowing that your data is protected from prying eyes. With these advantages, SafeShell VPN is an excellent choice for those who have faced the issue of their netflix vpn not working .
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To start using SafeShell Netflix VPN and enjoy content from different regions, follow these steps:
-
Begin by subscribing to SafeShell VPN. Visit the SafeShell VPN Website and select a plan that aligns with your needs and budget. Once chosen, click the "Subscribe Now" button.
-
Next, download and install the SafeShell VPN. Navigate to the SafeShell VPN website, select your device (whether Windows, macOS, iOS, Android, etc.), and download the corresponding app or software.
-
Launch the SafeShell VPN app and click "Log In" to access your account. SafeShell offers two modes, but for an optimized Netflix experience, select the APP mode.
-
Then, browse through the available servers and select one located in the region whose Netflix content you wish to access, such as the US, UK, or Canada. Click "Connect" to establish a connection to the chosen server.
-
Finally, open the Netflix app or visit the Netflix website. Log in with your Netflix account and start enjoying the streaming content available in the selected region.